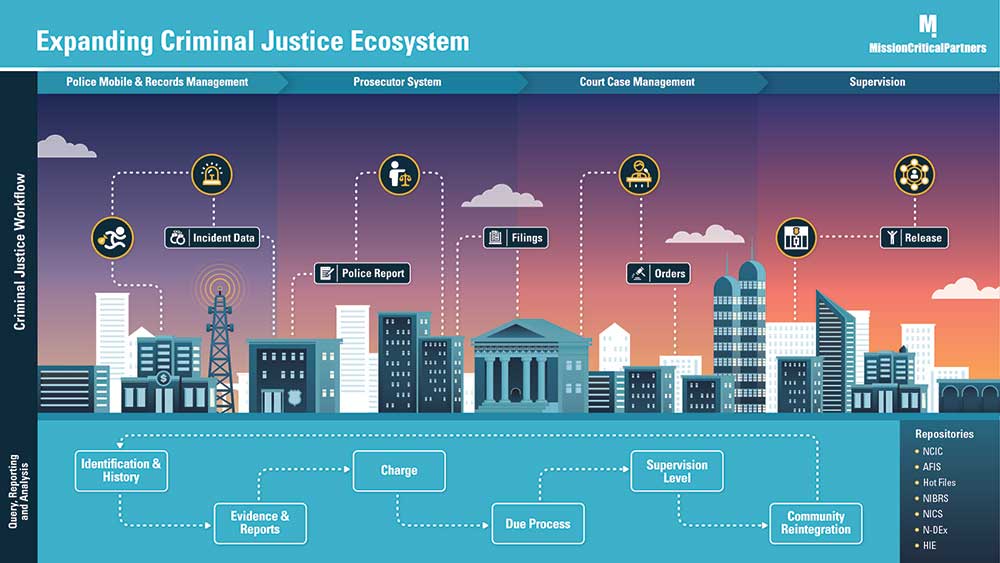
Improved Criminal-Justice Outcomes Driven by Better-Integrated Data Will Rebuild Citizen Trust
An incredible amount of data exists in the world, and it’s going to increase by orders of magnitude. In fact, some experts believe that the amount of data available worldwide will increase by 300 percent by 2025—a short five years from now. That’s truly mind-boggling.
On a high level, more and better data leads to enhanced decision-making and improved outcomes, regardless of one’s business. But at ground level, for data to be useful it needs to be “actionable,” because a tsunami of raw information would be unmanageable at best, overwhelming at worst. This is especially true in the public-safety and criminal-justice environments, where lives are on the line and every second matters. There’s simply no time, in the moment, to sift through a big pile of data and try to make sense of it.