Build a Smart PSAP Cyber Security Strategy: 8 Critical "Must-Haves"
Posted on September 5, 2017 by Mike Beagles
The emergency communications industry is a growing target for cyber security attacks and the threat is only just beginning. Public safety communications infrastructure is becoming more IP-based, and as a result, it's vulnerability to cyber threats is on the rise. There are more than 6,000 PSAPs located across the country, and 80 percent of them are small, making them unlikely to have inadequate cyber security defense programs. This is just one factor, among many, that makes 911 systems an attractive target for cyber-attacks.
Several major cyber security incidents have plagued the industry in the recent months, including
- An October 2016 attack where a teenager accidently impacted 911 centers around the country with a Twitter post containing a link that once clicked on, hijacked your iPhone and dialed 911 repeatedly. The post was clicked more than 117,000 times.
- Ransomware that affected 300 PCs and 40 servers with sensitive data plagued Madison County, who paid an astounding $21,000 in ransom (later covered by cyber insurance). The cost in
man-hours to restore data is unknown and irretrievable.
These are just two examples that demonstrate that cyber threats are growing in complexity and sophistication, and could continue to increase in severity as PSAPs become more interconnected, both regionally and at the statewide level.
So what cyber threats exist and what steps can you take to prepare your psap?
Understanding the types of cyber threats that exist today, PSAP and IT Managers can better protect the data and assets within their 911 centers that could be targets.
- Malware are computer programs that are designed to infect and damage computers without the user’s consent. These threats are more commonly-known as viruses, spyware, worms or Trojans. Malware infections typically originate via an email attachment or by clicking on a malicious web link that redirects the user to a website that is intended to spread malware on their computer and throughout its network to every ancillary servers and systems.
- Ransomware is a type of malware that locks your computer or certain files to prevent you from accessing your data until the attacker receives some type of financial gain, usually in the form of Bitcoin.
- Phishing is the act of attempting to acquire information, such as usernames, passwords and/or credit card details, by disguising as a trustworthy entity in an electronic communication. Typically, phishing attempts target an individual’s personal information such as social security numbers, passwords and other bank account information. Many of the larger, famous attacks within the news in the last several years have originated as phishing attacks—and are extremely complex and advanced attacks that are very difficult to eliminate.
- Device vulnerabilities can exist on any open device that connects to the internet, such as in-home security cameras, smart home devices like thermostats can have known vulnerabilities that can be openly exploited by cyber attackers. Mobile phones also fall within this category. For example, an employee’s mobile device that is connected to a PSAP’s Wi-Fi network could be a gateway into the PSAP’s network and can increase the cyber risk to the systems connected to that network.
- Social engineering is the act of obtaining or attempting to obtain otherwise secure data by deceiving an individual into revealing secure information. This can come in the form of a phone call, text or any type of outreach that is asking for private information on behalf of an entity they are impersonating, such as a bank or retail organization.
- Targeted attacks are malicious attacks targeted to a specific individual, company, system or software. The 911 system has already been the victim of several major targeted attacks and the rise of Next Generation 911 will likely intensify the threat. These attacks will typically come in the form of Distributed Denial of Service attacks (DDoS) that flood an emergency response network’s entry point, preventing 911 calls or text-to-911 messages being sent through the network.
Mitigation Strategies for your PSAP
It is without question that these threats present major risks. What practical steps can PSAPs take to protect their agency to decrease their vulnerability or likelihood of falling victim to an attack?
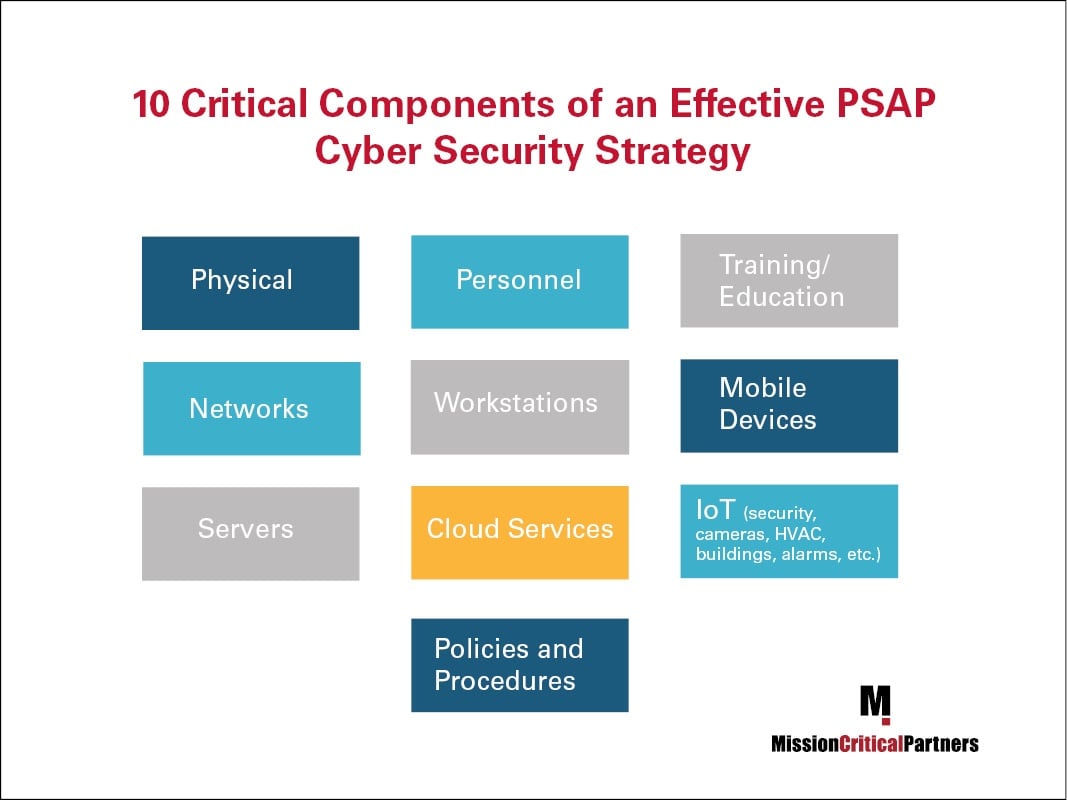
The first thing PSAP and IT managers must keep in mind is that if they are looking for one silver-bullet solution, either in the form of a device or an application, it does not exist. A PSAP’s strategy must be comprehensive and touch all the areas depicted in the graphic below at a minimum. As a PSAP and its technology and systems become more complex, this list will likely grow.
Here are eight critical “must-haves” agencies must work towards as when implementing a properly defined, comprehensive and multi-faceted cyber security risk prevention program:
- Define an individual, or individuals, to lead and be held accountable for the cyber security strategy. That person, or persons, must communicate and engage with the necessary boards and committees as well as the community, and should be the starting point for PSAPs looking to lead the effort in all necessary areas.
- A dynamic, extensive and accessible disaster recovery plan must be created that every individual and entity involved in the PSAP are familiar with.
- Internet usage policies must be defined, signed and followed by all PSAP employees and visitors.
- In the event the PSAP falls victim to an attack, data backups become very important to help you restore service quickly. Implement data backup policies that are viable and regularly-checked, and follow them.
- Go beyond Windows desktops when installing patches and updates. These must be installed on every single device and application in the PSAP and connected to the PSAP as soon as they become available.
- Employ two-factor authentication when possible on applications and systems in the PSAP’s work environment.
- Create audit logs for the PSAP’s application and systems that includes information such as user IDs, date and time of key events, such as log on and log off, files and networks accessed and successful and failed attempts. This information will prove to be useful in the event an incident occurs and needs to be investigated.
- Maintain an accurate inventory of all the systems and applications on your network that are being leveraged. Learn more about the importance of this in an earlier post, “What Public Safety Managers Don’t Know That Can Hurt Them.”
If you’re interested in learning more about how to protect your PSAP against today’s growing list of cyber security threats, we recommend viewing our recent webinar – which contains additional best practices – in it’s entirety. Or, if you’re looking to conduct an assessment of your organization’s cyber security program, please contact us.
Topics: Next Generation 911 Networks, Public Safety Technology, Continuity of Operations and Disaster Recovery