Cybersecurity Threat Advisory: China State-Sponsored Attacks on Networks and Devices
Posted on June 10, 2022 by Mike Beagles
A new critical security alert requires the mission-critical community’s immediate attention.
Advisory Overview
The National Security Agency (NSA), Cybersecurity Infrastructure Security Agency (CISA), and the Federal Bureau of Investigation (FBI) jointly issued an advisory concerning the ongoing efforts of cyberattackers sponsored by the People’s Republic of China.
What Is the Threat?
According to the joint advisory, these efforts center on exploiting common vulnerabilities and exposures (CVEs) to “establish a broad network of compromised infrastructure,” which then is used to exploit a wide variety of government, public-sector, and private-sector organizations worldwide, particularly telecommunications and network service providers. The following table, which is contained in the joint advisory, lists the top network device CVEs that China-sponsored cyberattackers are leveraging:
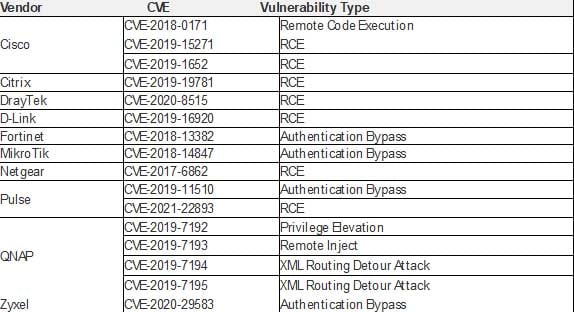
What Are the Recommendations?
The joint advisory, which can be read here, urges such organizations to execute the following mitigation tactics:
- Keep systems and products updated and patched as soon as possible after patches are released. Consider leveraging a centralized patch management system to automate and expedite the process.
- Immediately remove or isolate suspected compromised devices from the network.
- Segment networks to limit or block lateral movement.
- Disable unused or unnecessary network services, ports, protocols, and devices.
- Enforce multi-factor authentication (MFA) for all users, without exception.
- Enforce MFA on all virtual private network (VPN) connections. If MFA is unavailable, enforce password complexity requirements.
- Implement strict password requirements, enforce password complexity, change passwords at a defined frequency, and perform regular account reviews to ensure compliance.
- Perform regular data backup procedures and maintain up-to-date incident response and recovery procedures.
- Disable external management capabilities and set up an out-of-band management network.
- Isolate Internet-facing services in a network demilitarized zone (DMZ) to reduce the exposure of the internal network.
- Enable robust logging of Internet-facing services and monitor the logs for signs of compromise.
- Ensure that you have dedicated management systems and accounts for system administrators. Protect these accounts with strict network policies.
- Enable robust logging and review of network infrastructure accesses, configuration changes, and critical infrastructure services, performing authentication, authorization, and accounting functions.
- Upon responding to a confirmed incident within any portion of a network, response teams should scrutinize network infrastructure accesses, evaluate potential lateral movement to network infrastructure and implement corrective actions commensurate with their findings.
If you are looking for guidance, please reach out. MCP offers a comprehensive cybersecurity solutions suite for critical infrastructure organizations to help them determine their network, data, and application vulnerabilities. We can help you develop a complete cyberattack prevention strategy. Contact us today to learn more.
Topics: Cybersecurity


